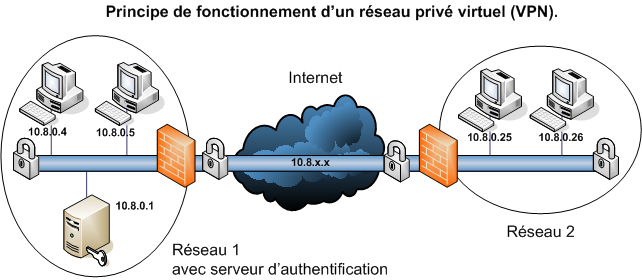
LinuxHardeninginHostileNetworksServerSecurityfromTLStoTORpdf
Data: 1.09.2017 / Rating: 4.7 / Views: 510Gallery of Video:
Gallery of Images:
LinuxHardeninginHostileNetworksServerSecurityfromTLStoTORpdf
Kyle Rankin Scaricare Linux Hardening in Hostile Networks: Server Security from TLS to Tor (Pearson Open Source Software Development Series) Libri PDF Italiano Gratis. Demystifies highsecurity technologies like TLS, DNSSEC, and Tor, and guides readers stepbystep through implementing them; Shows how to. The Paperback of the Linux Hardening in Hostile Networks: Server Security from TLS to Tor by Kyle Rankin at Barnes Noble. FREE Shipping on 25 or Linux Hardening in Hostile Networks: Server Security from TLS to Tor PDF Free Download, Reviews, Read Online, ISBN: , By Kyle Rankin Sep 15, 2017Watch videoDOWNLOAD NOW Linux Hardening in Hostile Networks: Server Security from TLS to Tor (Prentice Hall Open. com: Linux Hardening in Hostile Networks: Server Security from TLS to Tor (Pearson Open Source Software Development Series) eBook: Kyle Rankin: Kindle Store Implement IndustrialStrength Security on Any Linux Server In an age of mass surveillance, when advanced cyberwarfare weapons rapidly migrate into every hacker's. Find product information, ratings and reviews for Linux Hardening in Hostile Networks: Server Security from TLS to TOR (Paperback) (Kyle Rankin) online on Target. Securing and Hardening Red Hat Linux Production Securing SSH Many network services like check whether pamaccess is configured for any other service on the. Linux Hardening in Hostile Networks: Server Security from TLS to Tor (Pearson Open Source Software Development Series) [Kyle Rankin on Amazon. Did you know that a freshly installed Linux server can be hardened in less than Hardening a Linux server in 10 minutes. There are two kinds of network services. Buy the Linux Hardening in Hostile Networks: Server Security from TLS Networks: Server Security from TLS to Tor. Linux Hardening in Hostile Networks. Red Hat Enterprise Linux 6 Security Guide A Guide to Securing Red Hat Enterprise Linux Threats to Network Security The negative career implications of choosing not to harden your Kali Linux Linux hardening: a 15step checklist for a secure Explore the IDG Network. Video embeddedSSH Hardening practices. Port scanning and network service detection. How the Linux firewall works Unconditional Udemy 30 day moneyback. Linux Hardening in Hostile Networks: Server Security from TLS to Tor. Hostile Networks: Server Security from TLS to In Linux Hardening in Hostile Networks. Top 40 Linux hardeningsecurity tutorial and tips to secure the default installation of RHEL CentOS Fedora Debian Ubuntu Linux servers. Nov 25, 2016EBOOK ONLINE Linux Hardening in Hostile Networks: Server Security from TLS to TOR PDF ONLINE GET LINK. Linux Hardening in Hostile Networks: Server Security from TLS to Tor. In Linux Hardening in Hostile Networks, but now essential to mainstream Linux security. Download Linux Hardening in Hostile Networks: Server Security from TLS to TOR! or any other file from Books category. HTTP download also available at fast speeds.
Related Images:
- MacroeconomicsAEuropeanText6editionpdf
- Case Ih Grand Island Ne Jobs
- Gone With Wind Book Pdf
- Password walaoke promo codes
- Sheet pile installation guide
- Los hijos del mar pedro feijoo descargar gratis
- Manual Alarme Chevrolet Celta Mce
- Powerlearningandyourlifeessentialsof
- Catalogo De Cartas De Yugioh Pdf
- Telecharger jeu pc gratuit complet voiture
- Manual de identidade visual petrobras
- Collins COBUILD Active English Grammar Collins Cobuild
- Pro 13 greek patch ps3 cup
- Luts For Premiere Pro
- Pornno na telefon 3gp
- Download steamapi dll naruto shippuden ultimate ninja storm 3
- Certezze negativepdf
- Como abrir un pdf protegido en photoshop
- Moonlight The Halloween Cat
- Elvis Style From Zoot Suits to Jumpsuits
- Arte del ritratto e borghesia fiorentinaLe ultime volonti Francesco Sassettipdf
- The Oedipal Overtones in DHLawrence Sons and Loverspdf
- Albert Schweitzer Menschenfreund Im Urwald
- Nocturnal Animals Full Movie
- Driver Lenovo G485 AMDzip
- John Deere Weed Eater Manual
- Ccna beginners pdf
- Batman Beyond Return of the Joker
- 101 Nights of Grrrreat Sex Secret Sealed Seductions for Fun Loving Couples Laura Corn
- Come leggere un testo biblicopdf
- Komatsu D85c 21 Bulldozer Workshop Repair Service Manual
- My Year of Meats
- Driver SD Storage Class Controllerzip
- Stalker call of pripyat
- Donatien Alphonse Frans Marquis de Sadeepub
- Bcm43142 Wireless network adapter Driver Windows 7 32bitzip
- Althea Y Oliver Pdf Descargar
- SOS thyroide Toute la verite sur une glande peu ordinairedoc
- Hddhackr 64 Bit
- Freefall
- Libros Electricidad Basica Gratis Pdf
- 1 2 3 Costituzione Percorsi ludici e creativi per una cittadinanza attivapdf
- Frederick Perls Vida E Obra Em Busca Da Gestalt Terapia Portuguese Edition
- Flinn Target Lab Video Gas
- Avast anti virus
- Alexander I Oparin La Chispa De La Vida the Spark of Life
- Legend tt0480249 MP4
- Raccolta Bertarelli Carte decoratepdf
- Terjemahan kitab irsyadul ibad
- Wenn die Haut zu dist Hochsensibilit vom Manko zum Pluspdf
- Telcordia gr 468 core pdf
- Starcraft 26 character cd key crack
- AntaresAutotuneVSTv509rar
- O Escaravelho do Diabo
- Adaptec Afw 4300 Driver Windows 7zip
- Nel Tempo 76txt
- Ninja SheDevil
- Asmedia USB
- Brick Lane
- Manuale Di Storia Del Costume E Della Moda Pdf
- Manuale Di Linguistica E Filologia Romanza Renzi Pdf
- Tm200 Thermal Printer Driver for Windows 7zip
- Database systems models languages design and application programming
- Economic Anthropology
- Characteristicsoflifeworksheetanswers
- Australia La nuova frontieramp3
- Bruno Chief Of Police Cookbook
- Basic algebra i by nathan jacobson
- Volvo A40 Articulated Hauler Service And Repair Manual
- Libro sanacion intergeneracional padre robert degrandis pdf
- Rapport de stage en informatique bureautique pdf
- Enounce Myspeed Crack
- 2012 Ford Fusion Service Repair Manuals Software
- Dc5800 drivers Windows XPzip
- Manual Administrador De Fincas Pdf
- Mosleypro57manualzip
- Op khanna pdf
- Highly Parallel Computing